I also have all the passwords and logins for all the sites we use from AAA to our HOA site to airlines to social media networks, etc, etc. In addition, I also manage all of your digital media including photos, videos and important digital documents. Complicating the situation is that I run a business that is totally digital: blogging! I have several sites, tied to their own individual bank accounts and online identities spanning ad networks deals, social media pages, hosting sites, etc.Recently, the thought occurred to me that if I were to pass away or become incapacitated in any way, the family would be screwed. She wouldn’t know how many bank accounts we have, where the investments are, what online accounts we have or what stuff I have stored in the cloud (which is a lot). Plus, even if she did, she would not be able to log into any of them. This would mean that there would be a whole slew of digital logins and assets sitting around with no one to manage them or look after them. Our digital identity would be a complete mess.The only saving grace is that she knows my master password and has access to my two-factor authentication device, which she could use to access a list of all my sites and logins. However, she wouldn’t even know where to use the master password since she’s never done it before.In this article, I want to walk through some possible solutions that I researched over the last few weeks and how I decided to secure my digital legacy in case of my untimely death or demise. Not fun stuff to think about, but totally necessary especially since most of the stuff we do in our lives is online or in digital format.
Firstly, Get It All Together
No matter what route you take in the end to pass on information to your significant other or family member, you first need to get all the information together and store it in one place. Now there are a couple of ways to do this, but it’s absolutely necessary that the data is stored very securely since you’re basically putting your entire digital life in one location.Depending on your level of trust, you can generate this list either digitally or the old-school way. I use a password manager app that I feel confident won’t be hacked into. However, if you are just plain averse to putting such sensitive information online at all, then it’s best to simply write it all down or type it up and then print it and delete the digital version.The two best options for digital storage are KeePass and LastPass. KeePass can be stored locally and therefore might be a better option for those wary of storing everything on the Internet. If you’re comfortable with encryption and two-factor authentication, then you can use LastPass to compile all the essential data. LastPass has other useful security features like a one time password. With a one time password, you could store this in a secure location like a home safe and your spouse could use this password to log into your account if something were to happen to you. The nice thing about a one time password is that it expires after you log in once. So you don’t have to give out your master password nor store it anywhere that is not as secure as you would like.In terms of the information you should collect, it should literally be everything you can think of. Email accounts, online banking, credit cards, investments, social networking sites, airlines, shopping sites, backup sites, hosting sites, etc, etc. Basically anything you ever have logged into that still is pertinent and useful. With KeePass and LastPass, you can also add notes to each item you add, so if there is additional information other than login information you need to include, it’s easy to add that.
Secondly, Secure It All
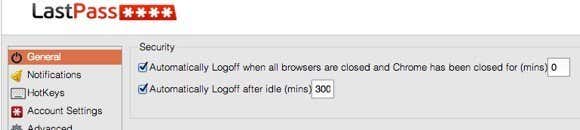
Now that you have a master collection of everything that exists in your digital life, you need to make sure it’s secure. If you’re using the digital options like LastPass or KeePass, you need to use more than just a strong password. Both have secondary authentication (two factor) options that make everything a million times more secure.Even with encryption and two-factor authentication, however, the data can still be compromised and this is where people wary of storing data digitally have a legitimate claim. For example, if you end up with spyware or malware that runs secretly in the background, it could easily capture everything you type in. In terms of actually getting access to your entire database, that would be much harder since the data is heavily encrypted by default. Even if the malware were to copy your database file to their computer remotely, they would not be able to crack it in any humanly feasible amount of time even with many fast computers.It’s essential that the computer you use to compile all of this information is clean before you start. If you’re doing a lot of copying and pasting, malware can capture what’s in the clipboard before it gets into the encrypted database. Also, if someone can remotely control your computer, then they can open the programs (if left open) and get all the information they need. That’s why it’s also essential to close the database if you’re not using it (KeePass) and to set a short timeout if you are using the browser extension (LastPass).With the LastPass browser extension, you can access everything right from your browser. This is convenient for logging into sites automatically, etc, but it also poses a big security risk. If someone takes over your computer and you’re logged into LastPass, they can just export a file with all logins and credentials and transfer it to themselves in a few minutes or less.However, LastPass knows of all this and therefore has lots of security options. For example, if you close the browser, you can make sure that LastPass logs out meaning if someone else comes by and opens the browser, they’ll have to login again. You can also have it so that it logs out after a certain amount of idle time. I set this to a few minutes because I don’t want the ability for someone else to access my account while I’m not there and the browser window is open. With KeePass, you also have quite a bit of security. The newest version even has the ability to confuse keyloggers installed on your machine so that they can’t actually capture the data you type into any of the fields. In addition to a master password, you can use key files. A key file is a file that is stored on an external device and needs to be used in addition to the master password to open the database. Lastly, you can link the database to your Windows account too, so even with the password and key file, you would aso have to be logged into that particular user account.That’s why pretty much everyone uses one of these two options for storing secure login information. If you don’t want to use any digital option, then simply write everything down on paper. I would highly advise against using a program like Word and then printing the file. The main issue being that while you are creating the file, it’s wide open to attack and not encrypted. Plus you have the chance of forgetting about it altogether, thereby opening yourself up to all kinds of problems. It will obviously take quite a bit of time to compile the list, so it’s best to use something secure while you do it.At a later point, after exporting the database to a printed version, you could delete the database or online account if you really felt uncomfortable.
Thirdly, Get a Lawyer
Unfortunately, the real world and the digital world are interconnected. When someone dies, the bank will usually freeze their accounts. If you don’t have the correct financial power of attorney set up, your wife may not be able to access any money until after the estate is settled. This can add more stress to an already super-stressful situation.A proper lawyer can get everything in order for you and can even be used to store your confidential master printed file or master password. What’s essential is getting all the power of attorneys setup correctly. A joint checking account will work, but that’s only if you have one bank account. In a case like mine, I have a bunch of bank accounts and only my name is on them. If I want her to take control, just giving her the login information will do nothing. Actually, it can cause more trouble because technically she’ll be breaking the law by accessing the accounts after my death.
Fourthly, Write a Guide & Store It
Lastly, you need to actually create something that someone non-technical can follow. The best way to do this is to write up a document that explains how things are setup, what accounts are important, how to access them, etc. Print this document and additionally, the list of all logins for everything and store this in a safe deposit box in a bank.Do not store this at home, even in one of those home safes if possible. Why? Well, it’s just better to keep it in an official location that requires someone to actually walk into a public place. If you have a safe at home and there are people who know what’s inside, it could cause someone to do something rash like force your trusted person to open it for them. It’s probably a small chance, but the fact is that crazy stuff happens after someone dies sometimes and you don’t want to be dealing with that.If you don’t want to actually store the entire password and login list in the safe deposit box, you can just keep the master password there or even just a single one time password, though that is a little riskier since it can only be used once and if someone gets locked out after that without getting the proper information, then they won’t ever be able to get back in.
Conclusion
This is obviously not the only way or the best way to transfer your digital identity to someone else after your death, but it’s a first step and one that most people, including myself, have never even bothered to think about. My wife and I created a will long ago with a trust and power of attorneys, but I realized that was only half of what she’ll need to manage everything properly.Let us know your thoughts if you’ve created a plan and what tools or processes you used for collecting and storing sensitive information. Enjoy!