Checksums are used to ensure the integrity of a file after it has been transmitted from one storage device to another. This can be across the Internet or simply between two computers on the same network. Either way, if you want to ensure that the transmitted file is exactly the same as the source file, you can use a checksum.The checksum is calculated using a hash function and is normally posted along with the download. To verify the integrity of the file, a user calculates the checksum using a checksum calculator program and then compares the two to make sure they match.Checksums are used not only to ensure a corrupt-free transmission, but also to ensure that the file has not been tampered with. When a good checksum algorithm is used, even a tiny change to the file will result in a completely different checksum value.The most common checksums are MD5 and SHA-1, but both have been found to have vulnerabilities. This means that malicious tampering can lead to two different files having the same computed hash. Due to these security concerns, the newer SHA-2 is considered the best cryptographic hash function since no attack has been demonstrated on it as of yet.As you can see in the screenshot above, the ISO file I am trying to download from Microsoft has a SHA1 checksum listed. Once I download the file, I would use a checksum calculator to verify the integrity of the file.About 99.9% of the time, you really don’t need to care or worry about checksums when downloading files off the Internet. However, if you are downloading something sensitive like anti-virus or privacy software like Tor, it’s probably a good idea to verify the checksum because hackers can create malware-infested versions of critical software in order to gain full access to a system.There are a ton of different utilities for calculating checksums and I’ll mention only one or two here since the good ones can create multiple hashes for you and can also verify hashes.
MD5 & SHA Checksum Utility
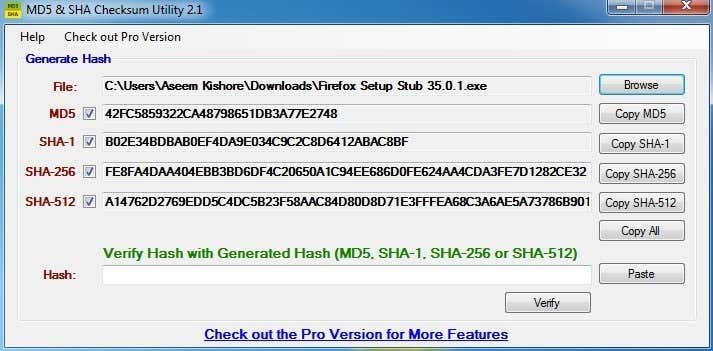
The MD5 & SHA Checksum Utility is my favorite utility for working with checksums because it has all the features I need in the free version. Once you download it, simply run the EXE file to open the program.The interface is very straightforward and easy to use. Simply click on the Browse button to choose your file and the hashes will automatically be calculated for MD5, SHA-1, SHA-256 and SHA-512.As you can see the MD5 hash is the shortest and the SHA-512 hash is very long. The longer the hash, the more secure it is.To verify a hash, just copy and paste it into the Hash box at the very bottom. Click on Verify and it will compare it to the four generated hashes to see if there is a match.
Online Checksum Calculator
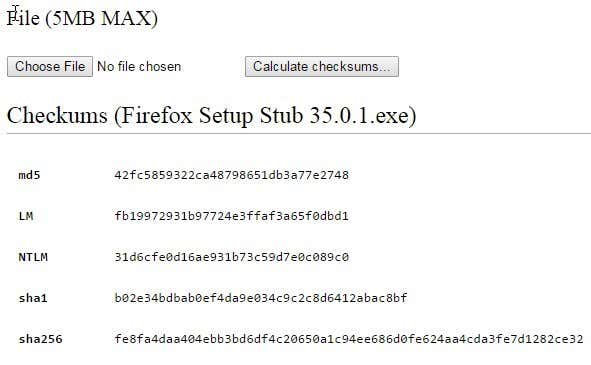
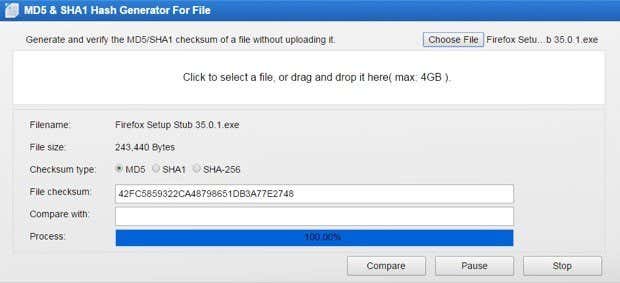
For those who would rather not download any software onto their systems, an online checksum calculator would be the better choice. The online calculators have more restrictions, mostly the max upload size of the file, but for smaller files, they work just fine.A site called Defuse has a free file checksum calculator for uploads up to 5MB in size. That’s pretty tiny, so you’ll need to use either the desktop application or the next online tool mentioned below for anything bigger than that.If 5 MB is just too small, then check out OnlineMD5, another free site that allows you to generate checksums for files up to 4 GB in size. Apparently, it does this without uploading the actual file to their servers. I’m not sure how it works, but it seems to just run the algorithm locally on your system and then just displays it in the browser. Quite a smart way to do it because you don’t have to download extra software and you don’t have to wait forever uploading a large file.This site is also very nice because you can verify a checksum in addition to just calculating one. Hopefully, you now have a better understanding of what a checksum is and how it can be used and calculated. If you are sending or receiving secure files, a checksum is the best way for both parties to verify the integrity of those files. If you have any questions, post a comment. Enjoy!